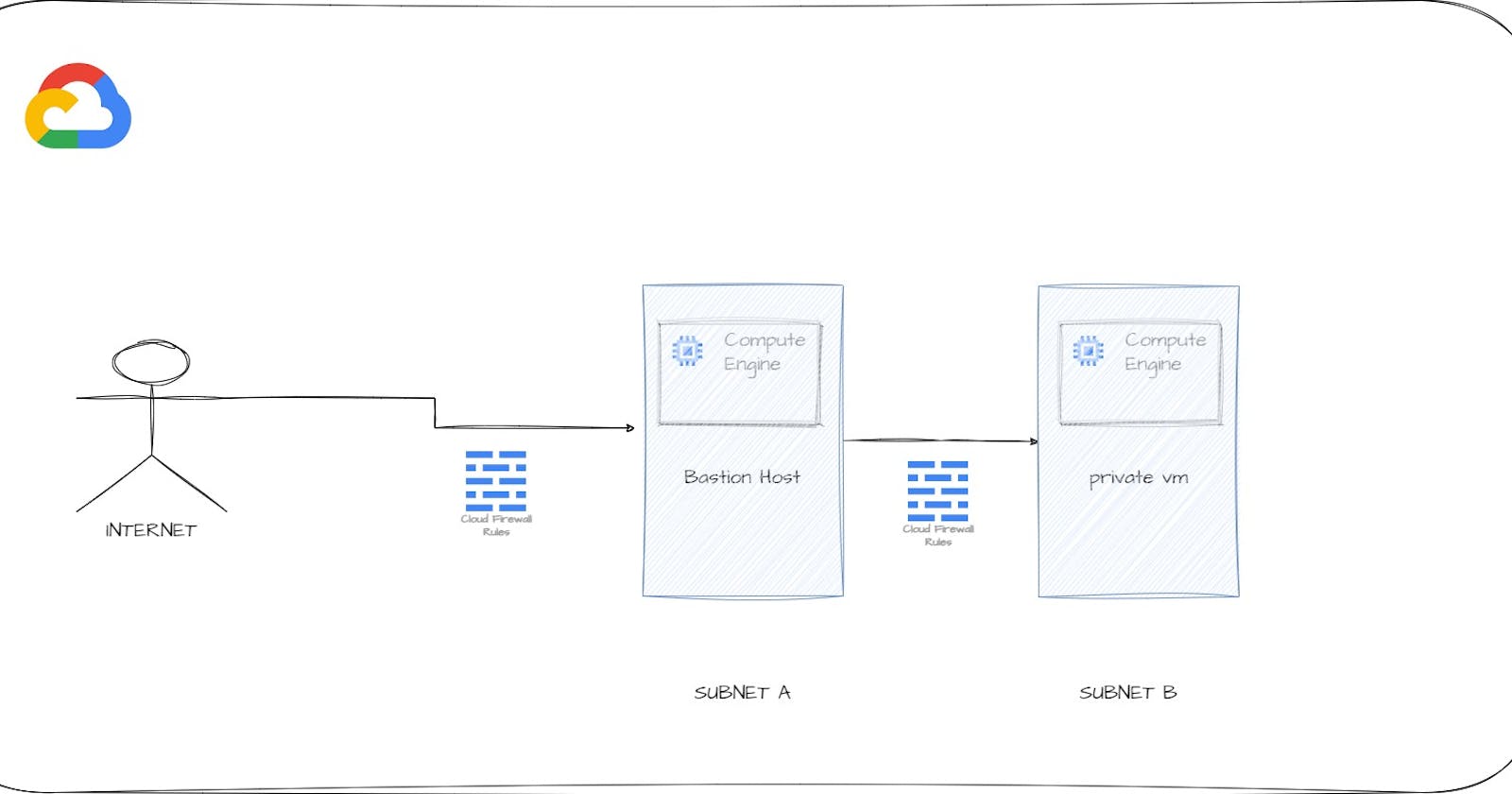
GCP Compute Engine with Bastion Host is a commonly used security configuration for providing secure access to virtual machines (VMs) in GCP. A bastion host is a special-purpose VM that acts as an intermediary between your local computer and the VMs you want to access.
SSH
Secure Shell (SSH) is a widely used protocol for accessing remote servers and computing resources. Google Cloud Platform (GCP) Compute Engine provides a powerful platform for deploying virtual machines in the cloud. In this blog post, we will explore how to SSH into a GCP Compute Engine instance using a Bastion host.
What is a Bastion Host?
A bastion host is a secure intermediary server that acts as a gateway for remote access to a private network. In the context of GCP Compute Engine, a bastion host is used to provide secure access to instances running in a Virtual Private Cloud (VPC).
Benefits of using a bastion host for accessing VMs in GCP
Enhanced security: A bastion host acts as a secure gateway to your VMs, reducing the surface area for attacks.
Centralized access control: With a bastion host, you can centralize access control and log for all SSH connections to your VMs.
Simplified management: A bastion host can reduce the complexity of managing SSH keys for multiple VMs.
Steps to set up Bastion Host
- Create a VPC network: Create a VPC network in GCP, which will be used to host your VMs and a bastion host.
gcloud compute networks create bastion-vpc \
--subnet-mode=custom
- Create two subnets in the VPC network
gcloud compute networks subnets create subnet-a --network=bastion-vpc --region=us-central1 --range=10.250.40.0/27
gcloud compute networks subnets create subnet-b --network=bastion-vpc --region=us-central1 --range=10.250.41.0/9
Note: Delete your default vpc before running the above commands
- Create a bastion host VM: Create a new Compute Engine instance that will act as the bastion host. Ensure that this VM is in the same VPC network as your target VMs.
gcloud compute instances create bastion \
--network=bastion-vpc \
--zone=us-central1-a \
--subnet=subnet-a \
--tags=bastion
- Create a private VM with no external IP
gcloud compute instances create private-vm \
--network=bastion-vpc \
--zone=us-central1-a \
--subnet=subnet-b \
--tags=private-vm \
--no-address
Create a Firewall rule to allow ssh to Bastion host with your IP address
gcloud compute firewall-rules create allow-ssh-bastion \
--allow=tcp:22 \
--network=bastion-vpc \
--target-tags=bastion \
--source-ranges=[YOUR IP_RANGE]
Create a Firewall rule to allow traffic from the bastion to all other instances
gcloud compute firewall-rules create bastion-fwd-private-vm \
--allow=tcp:22 \
--network=bastion-vpc \
--source-tags=bastion \
--target-tags=private-vm
SSH into bastion host and run below command to access private vm
gcloud compute ssh private-vm --internal-ip
Note: Make sure your bastion vm service accountt have Read/Write permissions.
That's it! You can now securely access your VMs in GCP using a Bastion host.
Conclusion
In this blog post, we have explored how to SSH into a GCP Compute Engine instance using a Bastion host. By following these steps, you can establish a secure connection to your instances running in a VPC. It is important to note that using a bastion host adds an extra layer of security to your system by providing an additional barrier against unauthorized access.